Comparing @OUCisco to @OUCyberSec
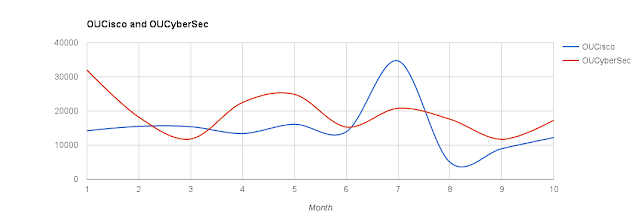
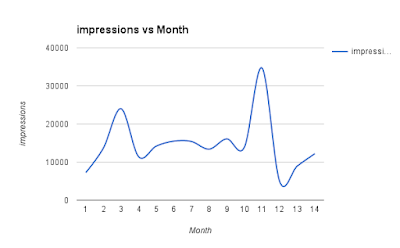
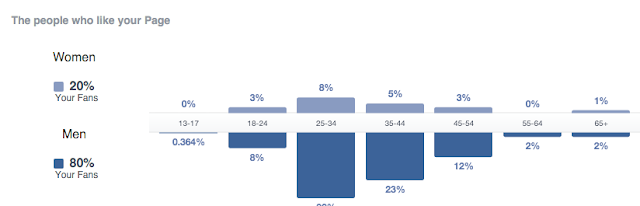
Some of you who follow me (and therefore this blog) may be aware that I curate two distinct twitter accounts @OUCisco and @OUCyberSec . Each attracts an entirely different community with some level of technical crossover. @OUCisco reaches out to Cisco Networking geeks and students primarily set at CCNA level there are some more advanced outputs during the summer. The twitter account and its other related social media profiles runs in sync with T216 an Open University Cisco CCNA module. It is designed to work with the October to June study calendar of our students - knowingly knowing that there are many others out there who also study the same programme in parallel. @OUCyberSec runs in sync with our FutureLearn Introduction to CyberSecurity MOOC . It runs for eight weeks around four times a year. Like our @OUCisco offering, the outputs are designed to follow the set study of the module aware that there are many out there interested in the broad topic of CyberSecurity. At the ti