Overnight passed 100,000 hits on my blog ...
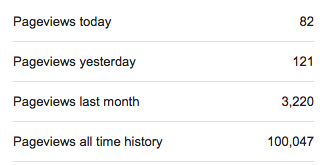
This may seem as if I am bragging (maybe one is), I am keen to share this for the benefit of other academics who are keen to blog yet seem to be stuck in a mortal coil. The data speaks for itself. Do I have a large interweb presence, I don't think so. Yet at different events, meetings, social gatherings I encounter interesting anecdotes from souls who read some of my articles. Amusingly they refer to articles that I have to take a moment to recall; not that I am particularly prolific. If you take a look at the following pretty picture, you can see that the experience is sporadic, some months are good, others not and it takes time to develop a following. The spike is some work promoted by Cisco Systems to their community, (11,000 hits), the dip was late last year early this year. The recent steady rise and higher level of hits has been as a result of my work with The Conversation . I typically average 2.5K to 3.5K hits per month, some up, some down, this is normal. As